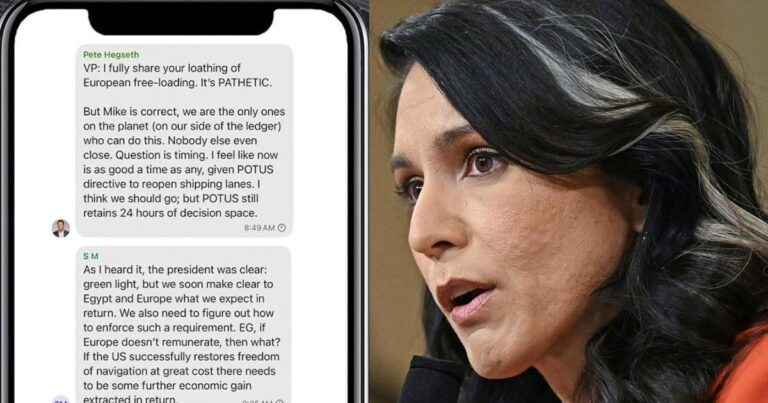
Hawaii Representative Tulsi Gabbard Addresses Controversy Over Signal Messaging Group Leak
Gabbard Denies Participation in Signal Group Amid Military Information Leak Allegations
Tulsi Gabbard, former Congresswoman from Hawaii, recently confronted accusations linking her to a private Signal messaging group implicated in the unauthorized release of classified military strategies. In a candid interview with PBS, Gabbard categorically rejected any involvement with the chat or the dissemination of sensitive war-related documents. She underscored her dedication to safeguarding national security and dismissed the claims as politically charged efforts aimed at undermining her reputation. Gabbard highlighted her history of advocating for transparency while responsibly protecting confidential information.
Her main assertions included:
- Refuting any membership or activity within the alleged Signal group
- Condemning leaks that jeopardize national defense
- Criticizing speculative media reports lacking concrete proof
- Expressing readiness to assist official inquiries
| Topic | Gabbard’s Stance |
|---|---|
| Leak of Military Plans | Firmly denounced |
| Signal Group Participation | Strictly denied |
| Media Coverage | Deemed politically motivated |
| Investigation Cooperation | Willing to cooperate fully |
National Security Risks Highlighted by the Leak of Classified War Plans
The purported exposure of sensitive war strategies through the Signal messaging platform has intensified concerns about the integrity of military communication channels. Security experts warn that such breaches can critically undermine tactical advantages, potentially revealing troop deployments and operational intentions to hostile entities. This incident exposes weaknesses in the current use of encrypted messaging apps by government and military officials, prompting questions about whether these tools provide adequate protection for top-secret information.
Major security challenges stemming from the leak include:
- Operational compromise: Adversaries gaining access to strategic plans could disrupt missions and endanger personnel.
- Strained international partnerships: Disclosure of joint operation details may damage trust among allied nations.
- Legal consequences: Individuals involved in unauthorized sharing may face investigations, penalties, or loss of security clearances.
| Security Issue | Potential Consequence |
|---|---|
| Vulnerabilities in communication platforms | Risk of interception by unauthorized parties |
| Insider leaks | Intentional or accidental exposure of classified data |
| Surveillance and tracking risks | Compromise of active military operations |
Insights from Cybersecurity Experts on Risks of Encrypted Messaging for Officials
Encrypted communication tools such as Signal are widely favored by public officials for their promise of privacy and ease of use. Nonetheless, cybersecurity professionals caution that these platforms are not impervious to breaches. Threats like social engineering attacks, compromised devices, and insider misconduct can still lead to leaks despite encryption.
Experts identify several critical vulnerabilities for officials relying on secure messaging apps:
- Verification difficulties: Confirming the true identity of chat participants remains challenging, increasing impersonation risks.
- Data persistence: Once messages are sent, they can be duplicated or archived indefinitely, reducing control over sensitive content.
- Multi-device synchronization: Linking accounts across devices can inadvertently create additional exposure points.
- Limited institutional oversight: Lack of formal monitoring mechanisms complicates accountability and leak investigations.
| Risk Element | Effect | Preventive Measures |
|---|---|---|
| Insider Threats | Leakage of confidential information | Implement strict access controls and thorough vetting |
| Device Security Breaches | Exposure through malware or hacking | Maintain updated security software and endpoint protection |
| Lack of Oversight | Delayed recognition of suspicious activities | Establish audit trails and continuous monitoring |
Strategies to Enhance Information Security Within Political Environments
In light of increasing incidents involving leaks through encrypted messaging services, political organizations must implement comprehensive security frameworks to protect sensitive communications. Essential steps include limiting access strictly to authorized individuals and enforcing robust identity verification for all participants in confidential chats. Educational initiatives aimed at improving digital awareness and recognizing phishing or social engineering tactics are vital to reducing accidental disclosures.
Technological enhancements can further bolster security by integrating:
- Advanced end-to-end encryption combined with stringent key management procedures.
- Real-time anomaly detection systems to flag and prevent unauthorized information sharing.
- Comprehensive audit logs to trace message origins and participant actions, facilitating rapid incident response.
| Security Issue | Suggested Solution |
|---|---|
| Unauthorized Access to Groups | Implement multi-factor authentication |
| Leaks via Third-Party Applications | Conduct regular app security audits and enforce restrictions |
| Unintentional Information Disclosure | Provide ongoing digital security training for staff |
Looking Ahead: The Ongoing Investigation and Its Broader Implications
As authorities continue probing the alleged leak of classified war plans, scrutiny over Tulsi Gabbard’s purported connection to the Signal messaging group remains intense. The PBS interview has illuminated the intricate challenges posed by digital communication in the realm of national security, sparking vital discussions about the balance between transparency and confidentiality. Observers anticipate further revelations as government agencies and policymakers work to clarify the facts and strengthen safeguards. Stay informed for the latest updates on this developing situation.